Endpoint Detection & Response
At the Point of Execution
Genian EDR. Where Execution Is Observed and Enforced.
when execution occurs
Retain Authority Over Data and Execution.
Genian EDR is designed for organizations that require full control over how security is operated, governed, and enforced. Unlike cloud-only EDR models, Genian EDR supports on-premises and hybrid deployments, allowing security data, policies, and response workflows to remain under your direct ownership.
At the point of execution, detection and response occur locally, without dependency on external processing or delayed cloud analysis. This ensures predictable enforcement, data sovereignty, and operational continuity, even in regulated or restricted environments.
From investigation to remediation, security teams stay in control of decisions, timing, and actions without surrendering visibility or authority.
Features
Actionable Threat Intelligence
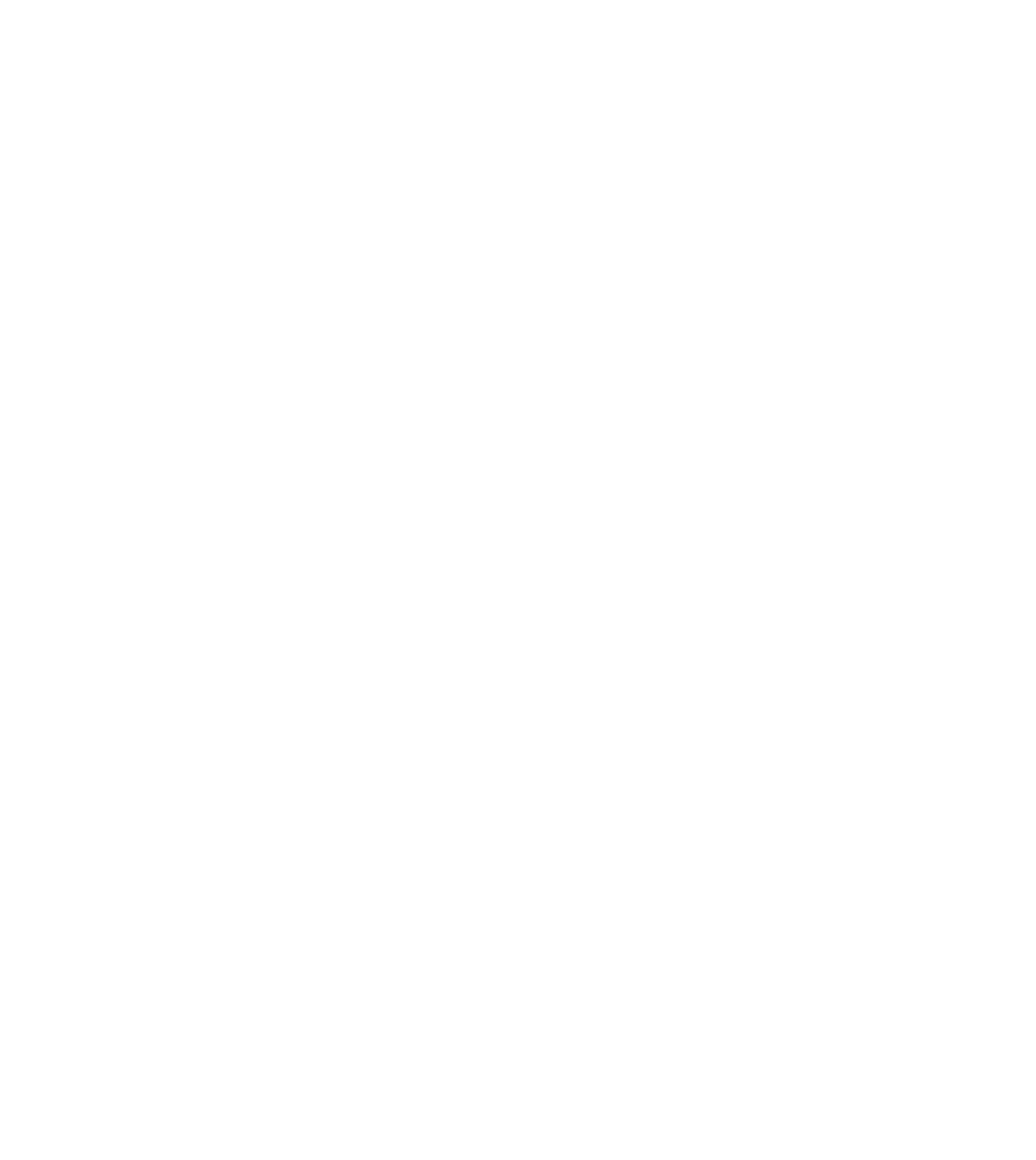
Monitoring Endpoints Behaviors
- Processing billions of events in real-time
- Endpoint activity monitoring: File, Registry, Process, DLL, etc.
- File information for peripheral devices (USB)
- Contextual, in-depth, and real-time analysis
- Customize data collection time and its respective retention period
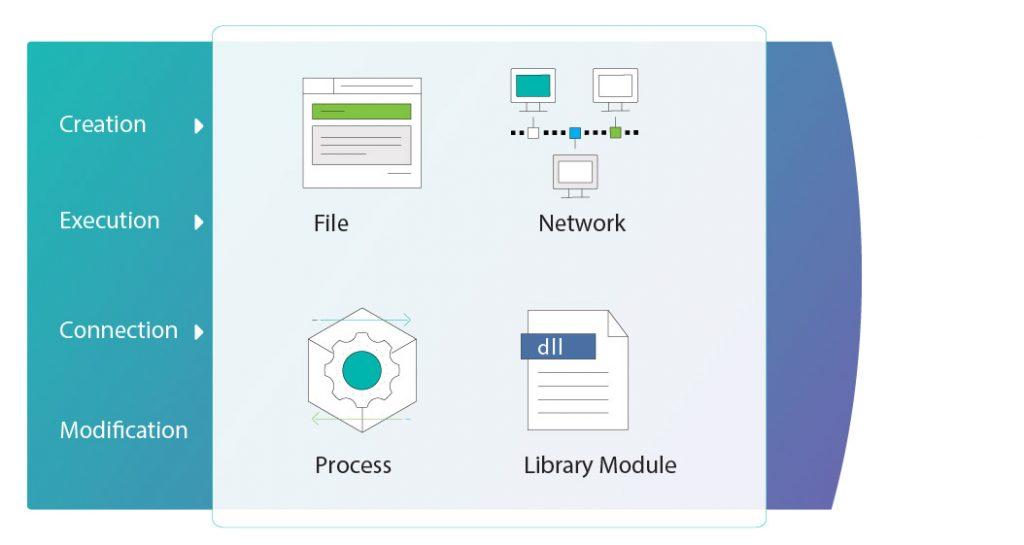
Detecting Threats
- Known threats by Indicators of Compromise (IOC)
- Unknown threats by Machine Learning (ML)
- Customized pattern matching by YARA
- X Behavior Analysis (XBA): Fileless threats by nonfile-based indicators such as particular execution events or behaviors
- Genian Ecosystem: Sharing file reputations, whitelists, alerts, and malicious data information among Genians’ customers to increase the accuracy of detection and decrease remediation time
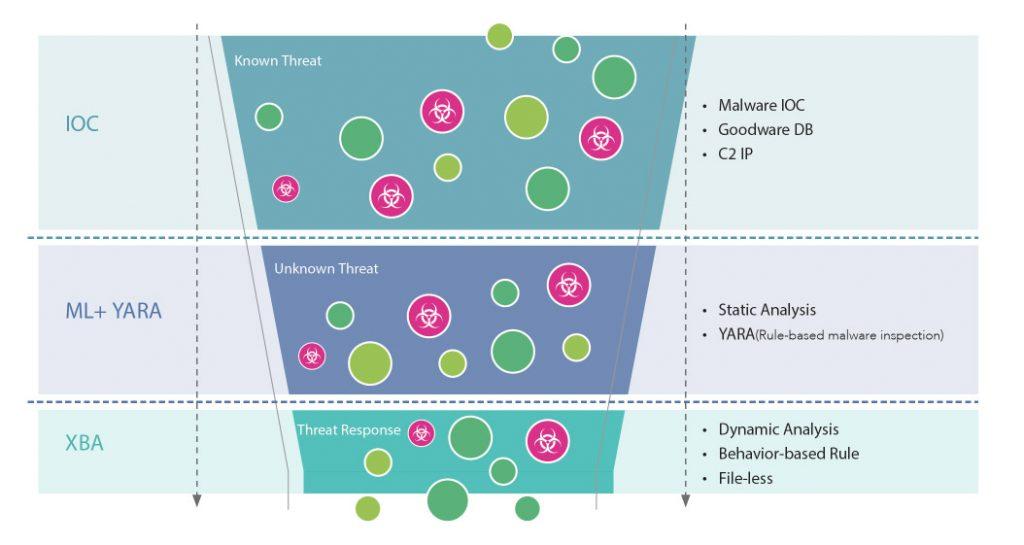
Interrogating Detected Threats
- Behavioral and heuristic analysis
- Consolidated threat information
- Integrated and relevant search engine
- Event timeline and chain of event correlation
- Third-party Cyber Threat Intelligence (CTI)
- Live response to access a compromised device immediately via a remote console for further in-depth investigation and countermeasures.
Visualizing X
- Personalized KPI dashboards using customizable widgets and libraries
- Instant search and filtering
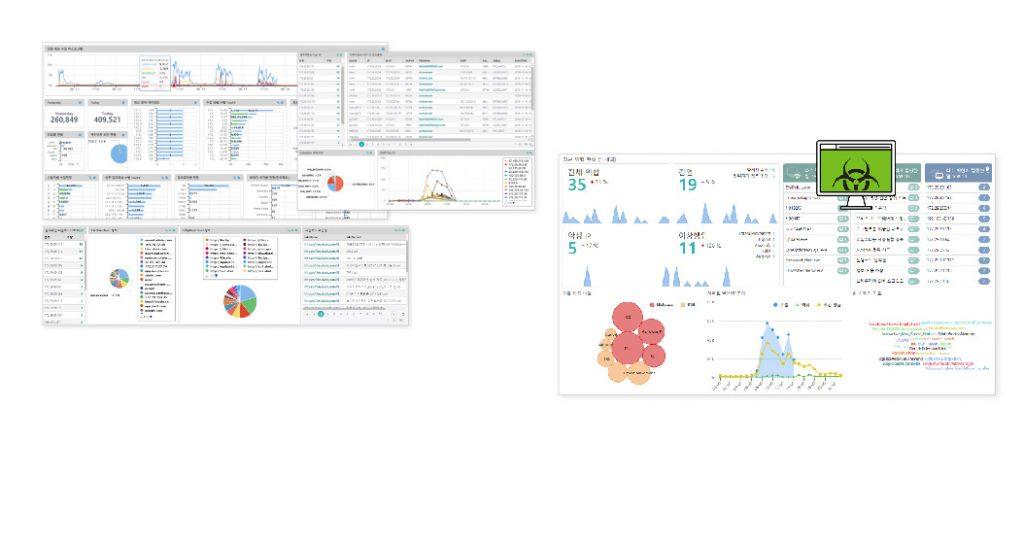
Automating Incident Response
- Automatic alert remediation (Alarm, Isolations, Quarantine, Terminations) for compromised devices
- Security orchestration
- Integrated with NAC solutions to prevent the expansion of threats at the edge
- Integrated with SIEM solutions to enhance intelligence
RESTful API, SNMP, Syslog support - Integration plugin support

Components
Seamless Protection. Zero Downtime.
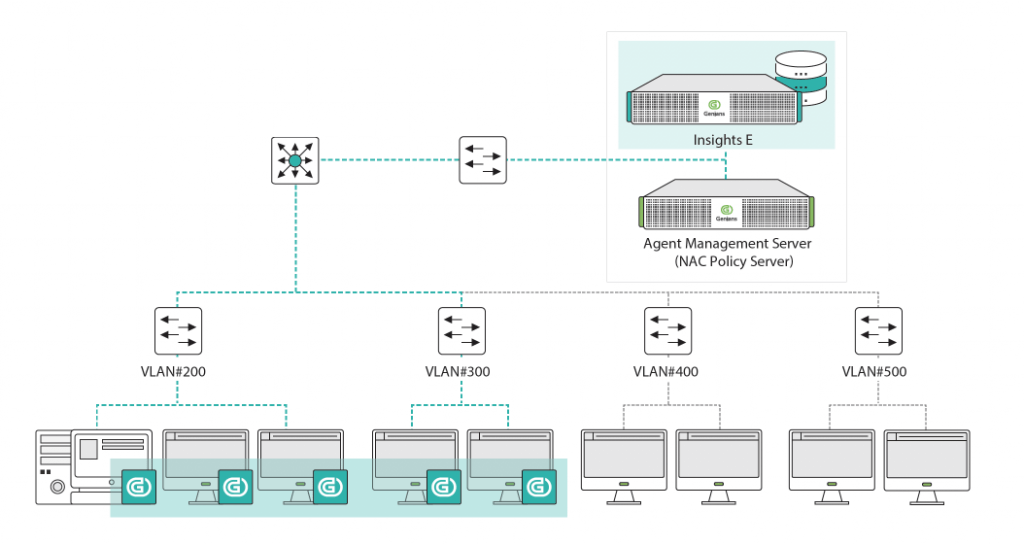
Genians Central Update Server
- Event Raw Data collected by E-Module store and backup
- Threat and anomaly detection
- Detected Threats analysis
- Comprehensive event analysis, Time series analysis, Root cause analysis
- Personalized dashboards and reports, customizable widgets
On-Premises EDR Server
- Auto detection and classification for all IP-enabled devices
- Policy-based access control
- Isolation and remediation for compromised devices at the network layer
- Integrated wired/wireless authentication
- Integration with user database systems
- Asset management for installed hardware, software, platforms, and patch
- IP address management
- Application-based comprehensive Agent
EDR Agent
- Endpoint activity monitoring: File, Registry, Process, DLL, etc.
- Collected data sent to Server
- Notification, alerts, process kill, access denial against threats at the endpoint layer
- Isolate compromised endpoint and lock down its user
Ecosystem
EDR That Connects. Security That Grows.
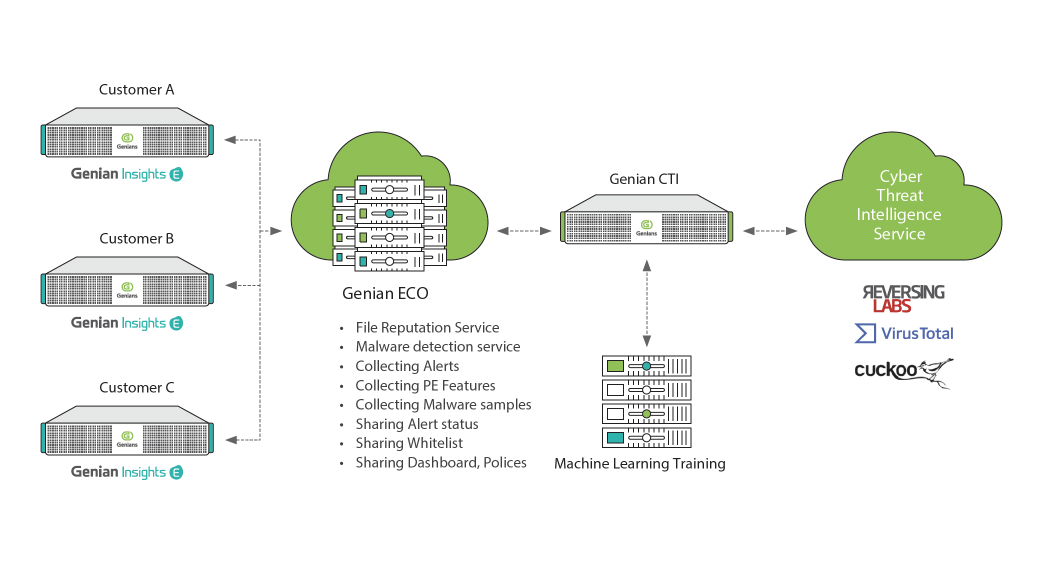
Genians’ Ecosystem collects threat information detected and reported from Genians’ customer sites. All collected information is aggregated and therefore anonymous.The refined information and reputation services can be shared with other customers right on time.
Integration
Maximizing EDR empowered by Next-Gen NAC
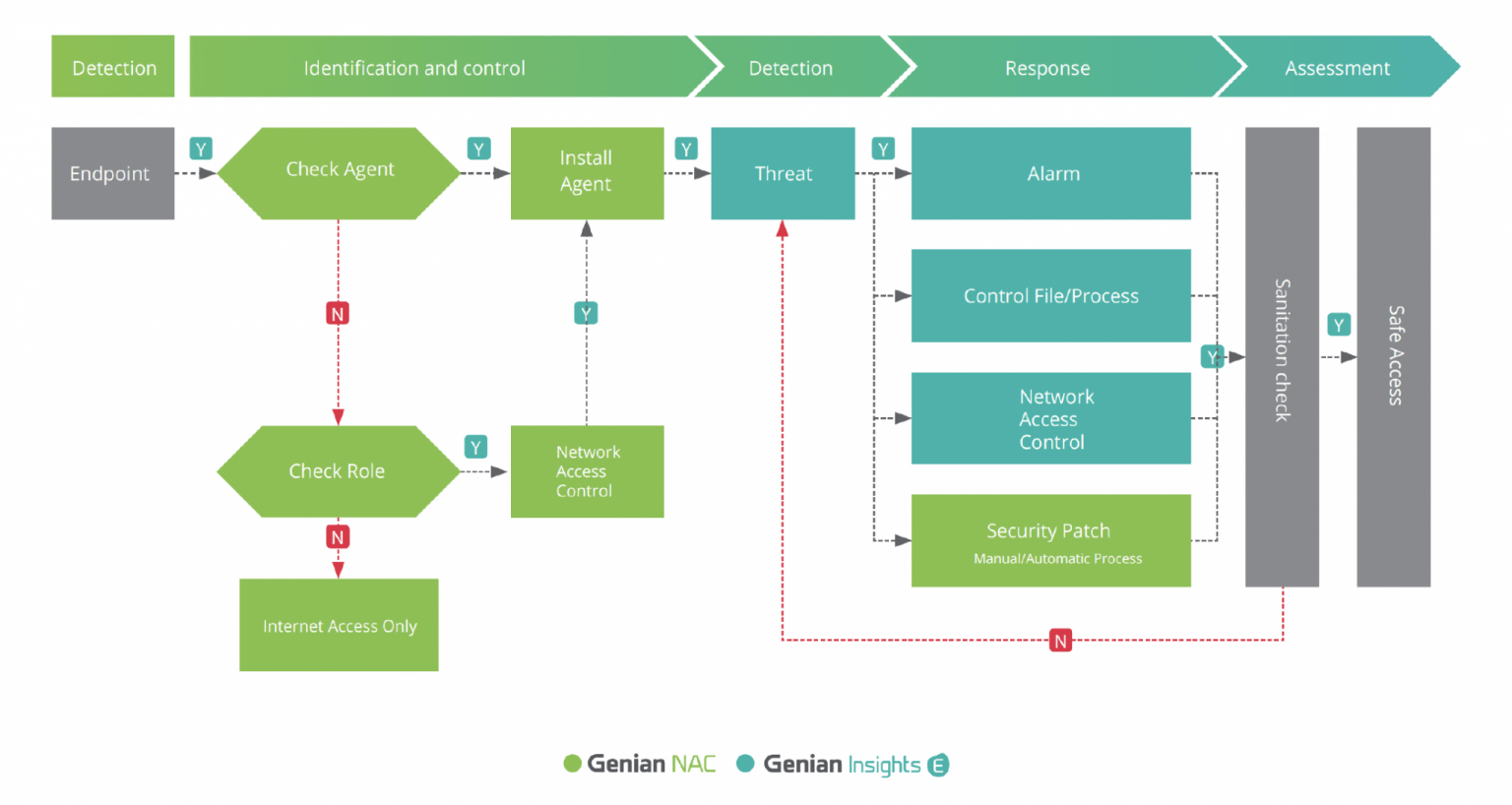
When Genian EDR integrates with Genian NAC, Genian EDR can gain better network visibility by identify and classifying all connected devices. Also, Agent actions can be maximized to respond threats more effectively.
Zero Trust in Action
Ready to Experience Genian EDR?
If you’d like to experience our EDR solution through a free trial, please contact us at hello@genians.com.
Our EDR team will guide you through the process and help you get started quickly.
